Cyber-attacks have long been a major source of concern for internet and computer aficionados. This is due to the various repercussions associated with such infections. To begin, WannaCry is a ransomware attack initially reported on May 12th, 2017. It targets computers using MS operating system. The attack spread on an unprecedented scale, resulting in the infection of more than twenty-three thousand computers in 150 countries. Some of the casualties of this cyber-attack include the Britain’s National Health Service, FedEx, Deutsche Bahn and Spain’s Telefonica.
What is Ransomware?

Many people have suffered the effects of a Ransomware. In brief, ransomware is a type of cyber-attack where the hackers take control of your computer actions, either by encrypting the files available or deleting them and asking for a ransom to be paid for the return of files. Cyber criminals gain access to the device within a network often through priming the victim to click on a link or downloading the virus by mistake. This is a gradual process where files are encrypted one after the other.
The first case of a ransomware was documented in 2005, thought to have originated in the United States. However, it quickly spread around the world. By encrypting the files on the hard drive of the computer, it makes it difficult for the owner to retrieve anything stored such as documents, music or files. Such criminals demand payments to decrypt or release the files, which are paid in the form of online cryptocurrency or bitcoins.
The WannaCry Encryptor
Also known as the wcry, it is a detailed ransomware plug-in that locks all the data on a computer system leaving the user with only two files. The two files include instructions to follow and the decryptor itself. Opening the software in the computer informs users that all their files have been decrypted. It then gives them few days to pay up. Otherwise, their files will be deleted. For WannaCry, the designers demand payment in Bitcoin, giving users instructions on the buying process and the address to send.
How it Spreads?
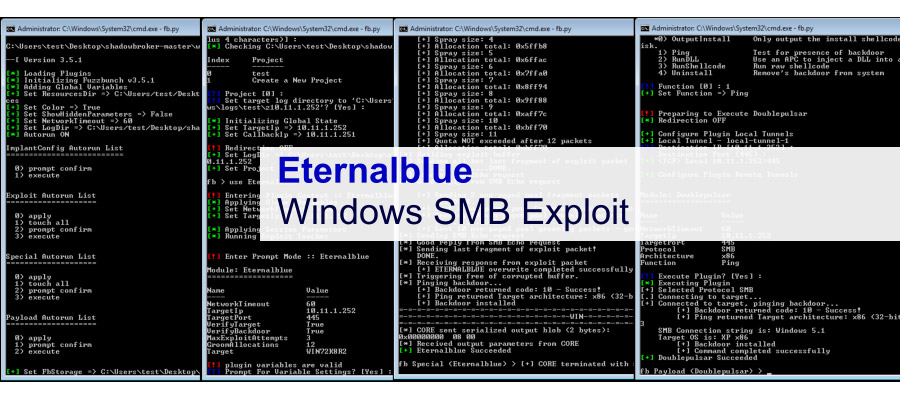
The WannaCry spreads across the internet and local networks. Main victims of this attack include systems whose security components are not up to date. WannaCry spreads using the EternalBlue exploit, a system that was developed by the US NSA and released by the shadow brokers two months prior.
It seems Microsoft anticipated the attack as it released a critical patch that removes the defenselessness for supported systems two months prior to the attack. Despite the presence of this patch, several organizations which haven’t applied it yet. Individuals with high risk included those who used systems with an older version of operating system including the Windows XP and Server 2003.
Elements of the Software
Like any other ransomware, there are various detailed technical write-ups about this WannaCry. As mentioned before, WannaCry targets computers running on Microsoft Windows. Some of the critical elements of this virus include:
- EternalBlue – This is the network infection vector of this virus. As mentioned before, EternalBlue was released by the shadow brokers, another hacker group, being an invention of the National Security Agency. This feature exploits the vulnerability of the MS17-010 in the Server Message Block protocol in Microsoft. The patch released by Microsoft two months before this attack fixed several versions of this system.
- DoublePulsar – It is a backdoor tool that was also released by the Shadow Brokers. The WannaCry code takes advantage of this tool to install it in the tool. By April 2017, reports indicated that several computers were infected by this backdoor tool.
- Kill switch – This acts as a terminator preventing security researchers from tracking activity from infected machines. This was an innovation by the proponents of this software to prevent security experts from studying the virus.
- Attribution – This component of the virus allows it shift blame as in a false-flag operation.
Defensive Response
Despite the innovative ways of the proponents of this virus to prevent the study, such as the use of a kill switch, there is a glimmer of hope for WannaCry victims. Security experts embarked on the ‘cure’ for this enormous killer virus hours after its spread. Several researchers including Marcus Hutchins, Benjamin Delpy, and Adrien Guinet focused on dealing with decrypting this virus.
Marcus Hutchins worked on a domain that helped in slowing the spread of this virus as stronger defensive measures were being deployed. Adrien Guinet stated that he was able to decrypt the ransomware running on Windows XP. He did this by discovering the prime numbers making up the WannaCry private key. However, this invention was not helpful at the moment as WannaCry was not running on Windows XOPP. It formed a new technique that would help future victims of this attack.
On the other hand, Benjamin Delpy came up with a fix called the Wanawiki. This program scours the computer memory for prime numbers that form the foundation for encryption. It then uses the prime numbers to generate unlock keys for the encrypted files.
See More: Go Live with YouTube Live Streaming Feature without Subscriber
Conclusion
The WannaCry came as a surprise cyber-attack to various countries. Some of the majorly affected countries include Russia, India, Ukraine and Taiwan. Recovering files after the infection is hardly possible. However, backup copies could help restore them. Deleted files could be recovered using the undelete tool.





