If you require an additional reason to worry about your phone’s protection: smart home gadgets, smartwatch, computer, and your phone, are in danger of simply being hacked anytime whenever the Bluetooth is “ON.”
The vulnerability, referred to as BlueBorne, had been found by protection study firm “Armis.” The experts could integrate an LG Sports Watch, Samsung Galaxy smartphones, a Google Pixel, and the car sound system through attacking Bluetooth, based on the statement.
The experts could remotely steal information through devices and seize control their cameras.
Additionally, the experts mentioned that some other devices are in danger, such as Samsung, Microsoft, Android, and iPads, and iPhones and Linux products which have not been already upgraded to the iOS 10.
Also, the BlueBorne assault just completes in about 10 seconds may split the Bluetooth-enabled gadget even though you may not a possibility linked to anything at all.
Armis states that Linux, Microsoft, and Google will certainly repair the issue in their latest patches. However, the breakthrough underscores the significance of vigilance in a progressively wireless and connected globe.
As the particular use of smart devices and Bluetooth offers comfort and ease all those luxuries are not necessarily without danger. This is now more vital than ever before to maintain your devices updated and to seriously consider to which features are allowed.
Therefore significantly, quit leaving the Bluetooth “ON.”
The complicated vector starts through discovering a device for hacking. It consists of making the gadget to give up details about it and after that, eventually, launch passwords and keys “in an assault that all a lot looks like heartbleed,” exploit which pushed numerous web servers to show passwords and some other keys distantly.
The next phase is the set of the code executions which allows for complete control of gadget. “This susceptibility lives in BNEP (Bluetooth Network Encapsulation Protocol) service that allows web sharing over the Bluetooth link (tethering).
Because of the flaw in service of BNEP, a hacker may induce the surgical memory problem, which is simple to exploit and allows him for running code on a device, efficiently granting him total control,” claims the experts.
Lastly, whenever the hackers have accessibility, they are in a position to start loading information through the device in the “man in the center” assault. “The vulnerability lives in PAN profile of Bluetooth stack, and allows the assailant to develop a malicious network user interface on the device of the victim, re-configure the IP routing plus force the gadget to transfer all communication from the interface of the malicious network. This assault will not need any pairing, authentication or user interaction making this invisible practically.”
iOS and Windows phones are guarded, and also Google users are getting a patch these days. Some other devices running old editions of Linux and Android might be susceptible.
How Can You Remain Safe?

Maintain almost all of the devices up-to-date frequently and be skeptical of old IoT devices.
Most of the time, the issues connected with the BlueBorne vectors ought to be patched through main players in electronics space however much less well-known devices might nevertheless be vulnerable to assault.
Switch Off Bluetooth While Not Being Used:
Even though leaving the Bluetooth continuously enabled can make utilizing your phone simpler. Additionally, it raises the danger of being the victim to the BlueBorne cyber-terrorist.
In case you can deactivate Bluetooth totally; this is a lot easier to keep Bluetooth turned off totally till the patch is launched.
Install Anti-Virus Application Now:
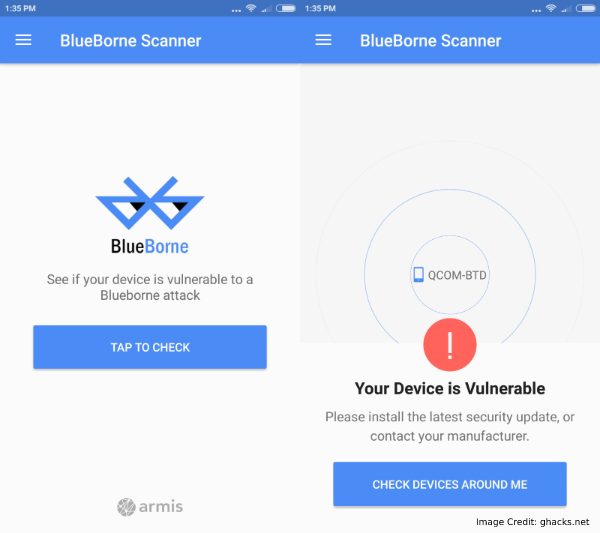
Awaiting an up-date for your Android mobile is not necessarily a choice. Till a patch is launched, your phone (and the data) is in danger of being cracked.
Keep in mind – it takes only 10 seconds for taking a complete control of the phone.
More Techno Scoop: How to Remove Random Items from Your Photo
Conclusion:
New options are required to tackle new airborne assault vector, in particular, those which make air gapping unimportant. In addition, people have to be much more research and attention because new protocols tend to be utilized for businesses and consumers as well.
Along with the high number of IoT, mobile, and desktop gadgets only growing, this is crucial that we are able to promise you that these kinds of vulnerabilities aren’t exploited, said Armis.





